FIVE OPEN-SOURCE TOOLS FOR SOC ANALYSTS
- Kelly Sharadin

- Sep 17, 2021
- 4 min read
The central pillars of every security operations center (SOC) are its people, processes, and tools. And while across SOCs there is standardization of people such as analysts or investigators andprocesses such as the incident response lifecycle, tools used by different SOCs tend to vary widely.
This means SOCs have flexibility in the tools they employ based on their requirements, available budget, and even preference. Given that, I have compiled a list of open-source tools found in both enterprise and small-scale SOCs that analysts should consider using to complete daily investigative tasks.
What is a SOC Analyst?
SOC analysts are the security “first responders”.They perform initial triage and analysis of incoming alerts and escalatethem for further evaluation in the event of a validsecurity incident.This role can be exciting and fast-paced, butit can also become quicklyoverwhelming due to information overload. Having a robust toolkit that streamlines investigations is imperative for analyststo effectively ingest mountains of information and make decisions in a timely manner.
Why Open-Source?
The disparity of tools in use across different SOCs means that analysts who become dependent on specific tools limit their long-term options. Open-source tools allow analysts to understand what is happening "underneath the hood," and this understanding can keep analysts vendor-agnostic or, in the event of court proceedings,allow the analyst toexplain the methods used during the investigation.
Aside from the cost (free), one of the great benefits of open-source tools are the communities who develop and freely shareinformation. Thisopen exchange of information can helpanalysts foster a solid methodology-first approach which is critical for career movement.The following are tools I use routinely in investigationsthat support a methodology-first approach.
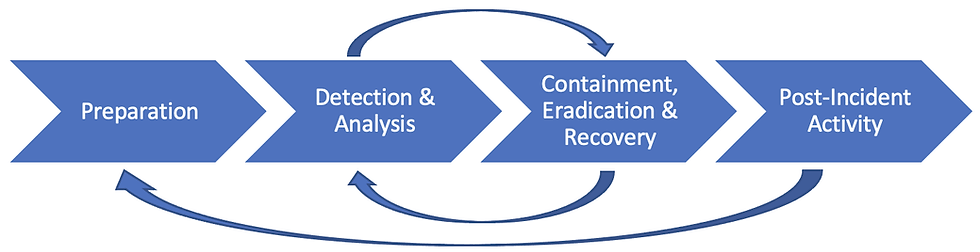
Each of the following tools ismapped to the Preparation, Detection, Analysis, and Containment phases of the NIST Incident Response Process for L1 and L2 analysts, a process security analysts are intimately familiar with.
ANALYSIS | Cyber Chef: "Swiss-Army Knife" for Digital Forensics and Incident Response (DFIR)
Cyber Chef is truly a one-stop shop for many DFIR tasks. Developed by an "analyst" and released by Government Communications Headquarters (GCHQ) located in the United Kingdom, Cyber Chef provides a single pane of glass to conduct daily incident response tasks such as examining email headers, decoding or encoding base64, extracting IOCs, de-obfuscating PowerShell scripts, or even generating simple hashes. Cyber Chef is available both as a web interface and local HTML application (recommended). A handful of GitHub repositories offer pre-canned "recipes" or ordered operations that can help automate investigations.
Warning: It is best practice to use Cyber Chef with caution when examining malicious scripts because the malware may attempt to reach out to other files on the host machine. If possible, deploy Cyber Chef in a virtual machine or sandbox disconnected from the network. Don't be that person who accidentally infects your company's network!
Resources: https://gchq.github.io/CyberChef/
ANALYSIS | Atom: Text Editor and Integrated Development Environment (IDE)
Having a text editor is essential for any analyst, but Atom’s customizability and no-cost barrier make it preferable to Notepad++ and Sublime Text. Atom is a fantastic way to have a streamlined local repository for Security Information and Event Management (SIEM) search queries or other scripts that you use daily. Atom has syntax highlighting extensions for Powershell, Python, and Splunk. Atom can also be configured to be a fully functional IDE to develop your own tools and is available for Windows, macOS, and Linux.
Resources: https://atom.io/
PREPARATION | KeePass XC: Password Manager
While a password manager may seem obvious, keeping all your passwords secure and organized is a must. As a security analyst, you will be given access to various shared resources between team members within the SOC in addition to your own tools. Effective organization of this information is pivotal for incident response.
If you are new to password managers, a walkthrough tutorial can be found here.
Resources: https://keepassxc.org/
ANALYSIS | Google Dorks: Search Engine Optimization Queries
Sometimes investigations will require you to gather as much information as possible to resolve a case. Google Dorks are a powerful technique that can be applied to any search engine, not just Google as the name would suggest. Google Dorks employ the use of targeted search operators to produce results not obtained by simple searches. View the resources link below to see how Google Dorks’ syntaxes are built and their use cases. Search engine syntaxes or Google Dorks can also be stored in your Atom text editor to enhance your threat-hunting playbooks.
Pro-Tip: Pagodo is an open-source tool that helps automate and evade Google throttling your IP for Google Dork searches by randomizing the interval in which searches are executed and by operating behind a proxy.
CONTAINMENT | DFIRtriage: Windows Remote Acquisition and Forensic Tool
Our list would be incomplete without a forensic acquisition tool. As the remote workforce continues to grow, having a working method for remotely capturing forensic data is an essential tool for modern SOCs. Developed by Travis Foley, DFIRtriage is a robust digital forensic acquisition tool for Windows incident response. DFIRtriage is a self-contained python executable that is dropped on the target host run as administrator and zipped up into a folder containing rich data to support investigations including scheduled tasks, network connections, persistence mechanisms, and more. DFIRtriage includes a suite of known and tested Windows diagnostic tools like Sysinternals.
Resources: https://github.com/travisfoley/dfirtriage
In Closing
I hope this overview of open-source tools was helpful. As we all know, cybersecurity is an ever-evolving industry. But while the tools themselves will continue to change, the underlying investigative methodologies will remain the same.
And for those responsible for managing a SOC, Pathfynder conducts table-top exercises to assess gaps and strengths within your security teams to best prepare against cyber threats. Please reach out if you are interested in testing your incident response plan or want to discuss these or other open-source tools to enhance your security operations!





Comentarios